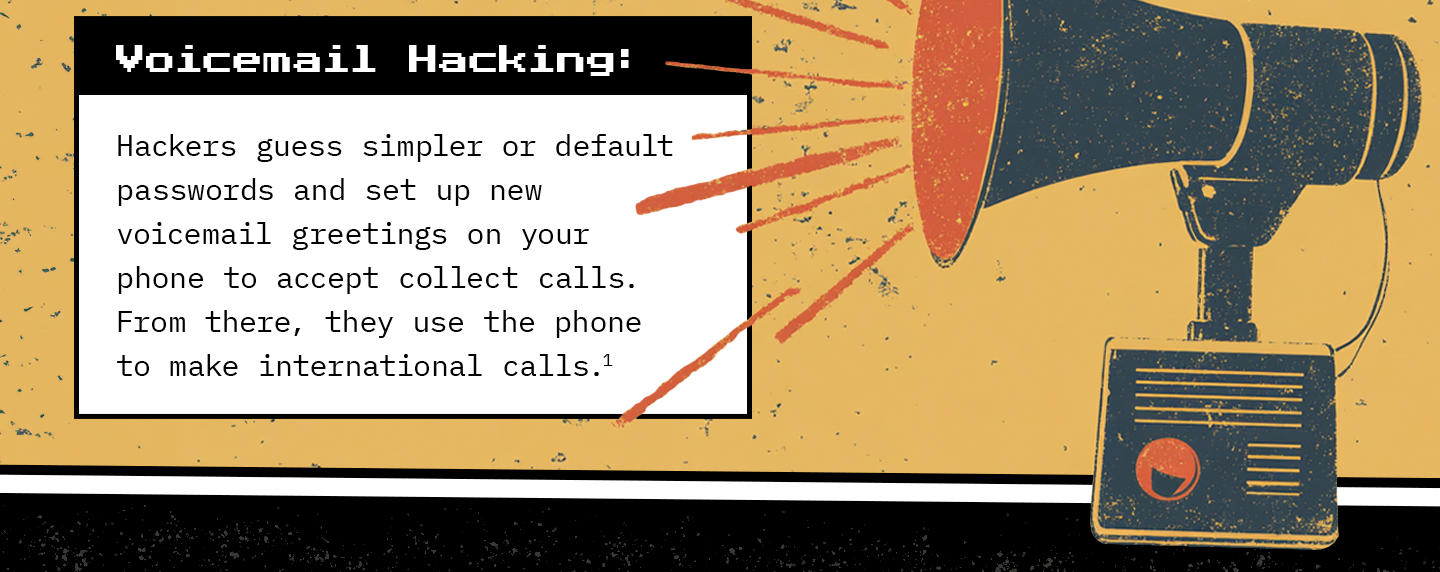
Glossary of Scam Terms



































Asking the right questions about how you can save money for retirement without sacrificing your quality of life.

Bucket lists don’t have to be for tomorrow.

Five overlooked tax deductions to help manage your tax bill.
A look at what you need to think about when buying a home.
How literate are you when it comes to your finances? Brush up with these five basics.
Net Unrealized Appreciation and how it affects tax responsibilities.
Determine your potential long-term care needs and how long your current assets might last.
Estimate the potential impact taxes and inflation can have on the purchasing power of an investment.
Use this calculator to compare the future value of investments with different tax consequences.
Peer-to-peer payment apps are one of the newest ways to send money.
Tulips were the first, but they won’t be the last. What forms a “bubble” and what causes them to burst?
A financial professional is an invaluable resource to help you untangle the complexities of whatever life throws at you.